September 15, 2022
CMMC 2.0
In 2020, the manufacturing industry saw a 300% increase in cyberattacks, and moved from the 8th most targeted industry by cybercriminals to the 2nd, behind only finance and insurance. That is not surprising, as manufacturing businesses harbor a wealth of information that hackers can use to extort millions.
With more than 250,000 Defense Industrial Base (DIB) companies and subcontractors involved in work related to the U.S. Government, a data breach presents a significant threat to sensitive federal and unclassified information, as well as to national security. Government agencies responded to the cyber threats by proposing stricter regulations for companies that protect sensitive data.
In early 2020, the Cybersecurity Maturity Model Certification and the IoT Cybersecurity Act were both introduced to ensure minimum cybersecurity regulations for companies that work with government agencies. The CMMC defines levels of cybersecurity required for DoD contractors to bid on and complete projects for the DoD. This certification ensures all companies and subcontractors who supply DoD establish a specific framework for cybersecurity, to protect the data that the DoD entrusts them with.
Not surprisingly, there have been changes to the program since CMMC 1.0’s introduction in 2020.
CMMC 2.0 includes five key changes to the program:
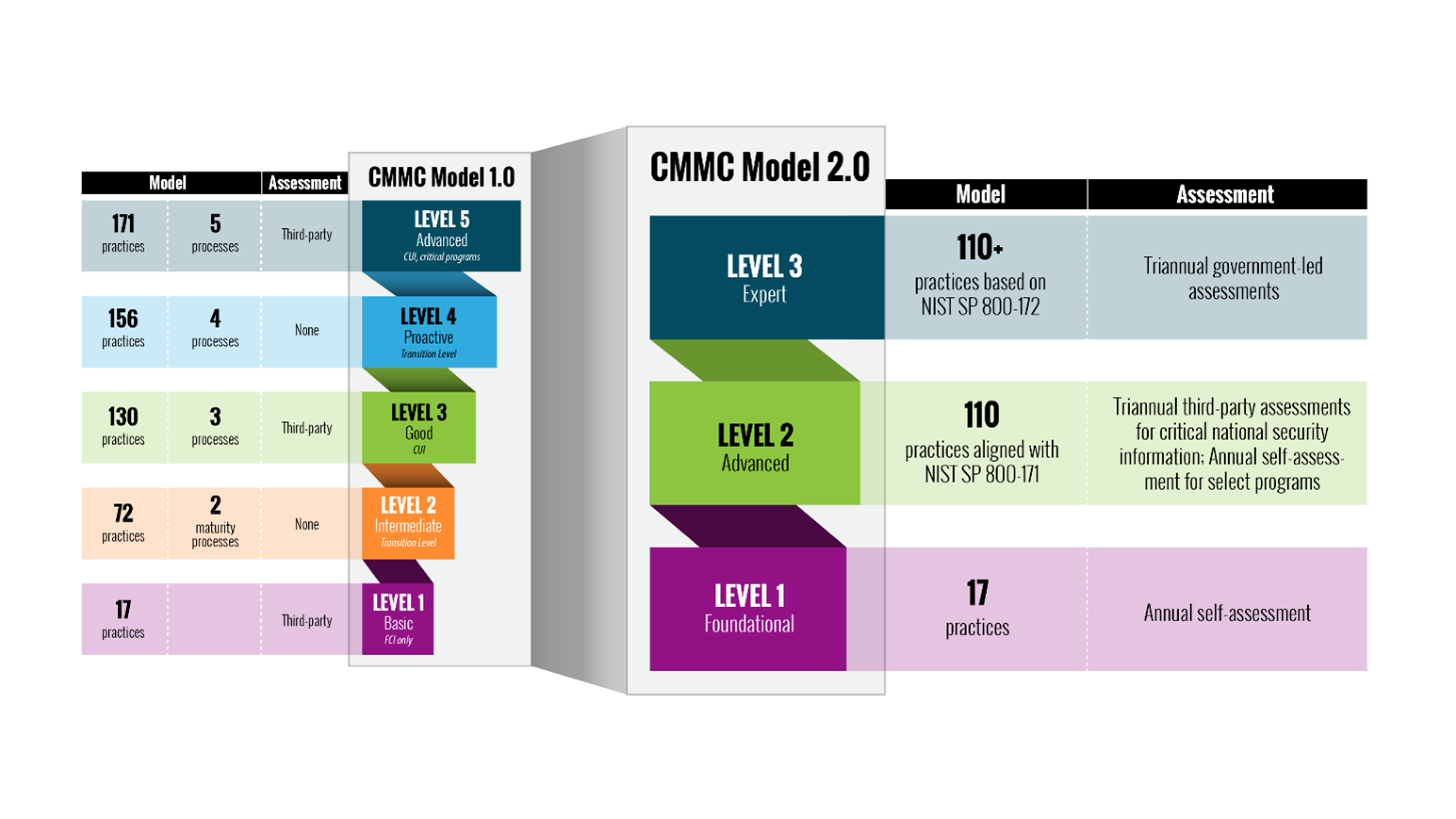
1. The CMMC now defines 3 levels of cybersecurity required for DoD contractors to bid on and complete projects for the DoD. (The new CMMC 2.0 levels are based on the type of information DIB companies handle)
- Level 1 (Foundational) only applies to companies that focus on the protection of FCI. It is comparable to the old CMMC Level 1.
- Level 2 (Advanced) is for companies working with CUI. Comparable to the old CMMC Level 3, Level 2 is in complete alignment with NIST SP 800-171.
- Level 3 (Expert) is focused on reducing the risk from Advanced Persistent Threats (APTs). Comparable to CMMC Level 5, it is designed for companies working with CUI on DoD’s highest priority programs. Specific security requirements are yet to be determined; however, the DoD has indicated that requirements will be based on NIST SP 800-171’s 110 controls plus a subset of NIST SP 800-172 controls.
2. While CMMC 1.0 included 130 practices, CMMC 2.0, introduced in November 2021, is a 1:1 reflection of NIST SP 800-171, with 110 practices. The 20 practices added by the DoD have been removed.
3. CMMC 1.0 only let contractors and subcontractors pass with a perfect assessment score. Theres was no flexibility to remediate. CMMC 2.0 allows contractors and subcontractors to sign DoD contracts using the Plan of Actions and Milestones (POAM). Organizations who have not yet fully implemented NIST 800-171 can submit a solid plan for achieving full compliance, with specific dates and a timeline. This POAM is submitted before work begins and enables organizations to begin working for federal agencies whilst they simultaneously work towards full implementation of 800-171.
4. The maturity level is no longer based on processes and policies, but on practices used.
5. The maturation model was restructured from 5 levels to 3, to better reflect how mature and reliable a company’s cybersecurity infrastructure actually is.
- Level 1: Self-assessment is no longer required to be conducted by a third-party assessment organization and will be valid for one year.
- Level 2: An assessment conducted by a third-party assessment organization is good for three years.
- Level 3: Has not yet been developed and will be based on NIST SP 800-172.
As threats grow, and companies address cybersecurity regulations enforced by NIST and outlined by recently introduced legislation, companies who fail to address cybersecurity will fall behind. Even worse, these unprepared organizations may become easy targets for cybercriminals.
If you have any questions related to CMMC compliance, contact DataSure24 at info@datasure24.com.