SERVICES

CMMC Services
CMMC 2.0 enforcement begins November 10, 2025. If your business contracts with the Department of Defense, compliance is not optional. DataSure24 provides comprehensive CMMC services to help you prepare, meet requirements, and maintain certification with confidence.
Our CMMC Service Suite
CMMC Scoping
Define your CUI boundaries, establish assessment scope, and create data flow diagrams (5-6 weeks).
Gap & Mock Assessments
Identify control gaps, develop POA&Ms, and conduct dry-run certification assessments (5-8 weeks).
CMMC Readiness Programs
Complete 12-month program development for Levels 1 and 2, including policy creation and oversight.
Certification Partnerships
Direct alignment with C3PAOs to ensure a swift certification process and assessment support.
Policy & Procedure Development
Create all required documentation, SSPs, and compliance artifacts.
Continuous Monitoring & Support
Ongoing advisory services to maintain compliance post-certification.
Why Choose DataSure24 for CMMC?
- Certified Expertise: Our team includes lead CCAs and provisional instructors (PIs) with over 25 years of NIST 800-53 auditing experience.
- End-to-End Support: From initial scoping through certification and beyond, we’re your complete CMMC partner.
- Proven Process: Our structured approach ensures you’re assessment-ready on schedule and within budget.
- C3PAO Partnerships: Direct relationships with accredited assessors eliminate delays and uncertainties.

Email Security
Your First Line of Defense Against Cyber Threats
Email remains the No. 1 attack vector for cybercriminals, with over 75% of ransomware attacks starting through malicious emails.
From sophisticated phishing campaigns to business email compromise (BEC), your inbox is under constant assault.
DataSure24’s Email Security service, powered by Check Point’s industry-leading technology, provides the comprehensive protection your organization needs.
What Makes Our Email Security Different?
Pre-Delivery Protection:
Unlike traditional solutions that scan emails after delivery, we analyze threats in line — before they ever reach your inbox. This crucial difference means malicious content never touches your environment.
AI That Learns and Adapts:
Our advanced AI and machine learning algorithms analyze every email component in real time, achieving an industry-leading 99.2% catch rate for phishing attacks. The system continuously learns from new threats, staying ahead of evolving attack methods.
Comprehensive Protection Features
Advanced Anti-Phishing:
AI-powered analysis detects even the most sophisticated phishing attempts, including zero-day attacks and social engineering
Malware & Ransomware Prevention:
Multilayer security quarantines dangerous files and attachments before delivery
Account Takeover Protection:
Behavioral analysis monitors over 100 indicators to identify compromised accounts
Data Loss Prevention (DLP):
Smart DLP identifies and prevents unauthorized sharing of sensitive information
Business Email Compromise Defense:
Historical email analysis prevents impersonation and fraudulent requests
Complete Collaboration Security:
Protection extends beyond email to Microsoft Teams, SharePoint, OneDrive, and Google Workspace
Real Business Benefits
Reduced Risk:
Stop threats before they cause damage, protecting your data, reputation, and operations
Improved Productivity:
Less time dealing with spam and threats means more time for real work
Regulatory Compliance:
Meet industry requirements for data protection and privacy
Lower IT Burden:
Automated threat handling and 24/7 expert support reduce strain on your team
Complete Visibility:
Detailed reporting provides insights into threats and security posture
Seamless Integration & Support
Our email security integrates smoothly with your existing infrastructure:
Microsoft 365:
Full protection with minimal configuration
Google Workspace:
Comprehensive coverage for all Google services
Hybrid Environments:
Supports both cloud and on-premises email systems
Deploy in minutes, not days. Our team handles the implementation while you maintain full control through an intuitive management portal.
Expert Support When You Need It
With DataSure24’s Email Security, you’re never alone. Our service includes:
- 24/7 incident response support from certified security experts
- Rapid threat analysis and remediation (typically under 10 minutes)
- Continuous monitoring and proactive threat hunting
- Regular security updates and threat intelligence briefings
Ready To Secure Your Email?
Don’t wait for a breach to realize your email security isn’t enough. Contact DataSure24 today to learn how our Email Security service can protect your organization from today’s most dangerous threats.

Chief Information Security Officer (CISO)
DataSure24 understands that every organization has different strengths and weaknesses. As the Fractional CISO, DataSure24 will be responsible for the oversight and management of your cybersecurity program, and will work with you to build your cybersecurity program from the ground up.
Our CISO program begins with conducting a cybersecurity assessment to determine an organization’s strengths and weaknesses, compliance with any requirements, and overall security posture. Based on the findings, we then work with company representatives to develop a system security plan that best meets an organization’s needs.
CISO Responsibilities Include:
• Cybersecurity Program Oversight, Monitoring and Administration
• Thoroughly document cyber threat protections and tools used
• Identify any weaknesses in the threat protections and recommend areas for improvement
• Develop information security policies and procedures
• Conduct log analysis of event data
• Maintain a cybersecurity program that protects the organization and is in accordance with any applicable compliance requirements
• Review current security awareness training program and change or develop where necessary
• Conduct incident response training with staff
• Report to board of directors/management annually
CISO Stages
At DataSure24, we focus on a 4-phase methodology to deliver CISO services to our clients.
1
• Security Assessment
• Compliance Baseline
• System Security Plan
2
• Policy & Procedures
• Patch & Vulnerability Management
• Security Awareness Training
3
• Security Controls & Tools
• Vendor Risk Management
• Incident Response Planning
4
• Change Management
• Advanced Security Options
• Security Process Optimization
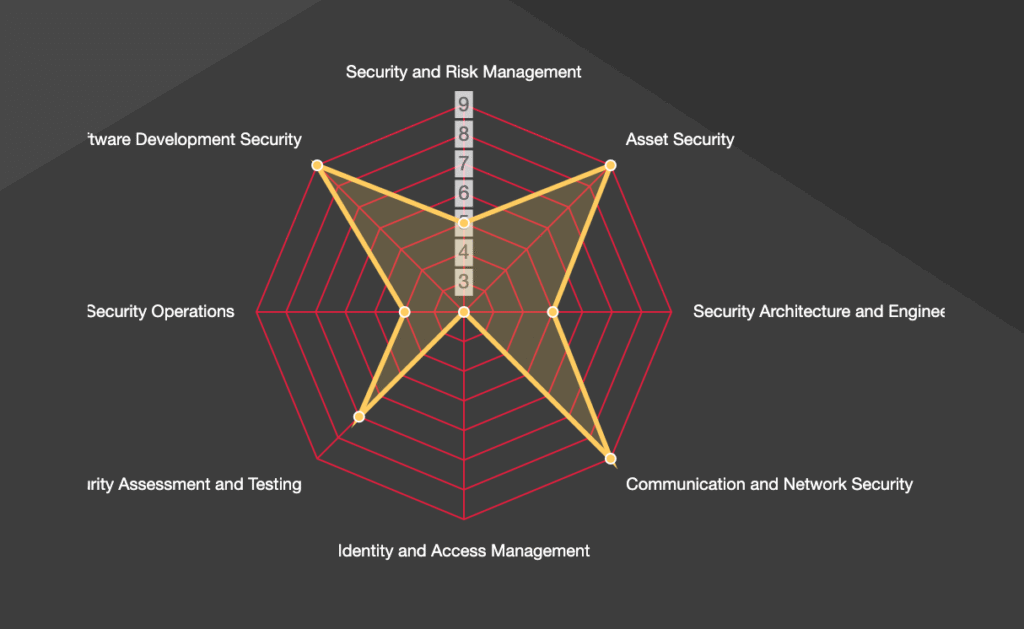
A cybersecurity assessment helps to determine a business’s strengths and weaknesses, compliance with any requirements, and overall security posture. Based on the findings, a CISO will develop a System Security Plan (SSP) which identifies and scores various focus areas based on a numbered scale, creating a web-like pattern.
Every business is not only different, but an individual business’s needs may change over time, leading to differences in the SSP’s appearance.

Cybersecurity Assessment
Regardless of how old a business’s cybersecurity program is, it’s important to regularly assess its current security posture, its operational processes and policies and procedures. Simply put, you can’t protect your business if you don’t know what gaps are present and where they are.
Every business is different, so completing a Cybersecurity Assessment will allow you to answer the following questions:
• What is my company’s critical information?
• What controls are in place for information systems?
• What is the current security posture of information systems?
• Should more or less stringent countermeasures be instituted?
• What is the prioritized security roadmap to follow that addresses high-priority issues first?
• Where am I at with my compliance requirements, and what should be next?
DataSure24’s team of security analysts have more than 20 years of experience navigating the complexities of cybersecurity assessments. Our risk assessments are based on cybersecurity frameworks developed to protect controlled unclassified information, including:
• National Institute of Standards and Technology (NIST) special publication 800-171
• Defense Federal Acquisition Regulation Supplement (DFARS)
Although all organizations aren’t required to comply with the same frameworks, alignment of security and control structures against recognized frameworks is a key step in process maturity and diligence. After completion of risk assessments, company personnel receive case-specific recommendations for improving the company’s security posture, as well as meeting regulatory compliance.

Penetration Testing
DataSure24’s Security Analysts conduct vulnerability scans to identify gaps in a company’s security program. The results are used to attempt exploits against the organization, mimicking a real-world scenario of what could happen if gaps in security are left unaddressed.
Penetration Testing follows a five-step methodology, with the procedures involved in each step driven by the specific needs of the individual company.
1
Planning
Scoping, boundaries, communication procedures, authorizations. Identify the best approach for testing.
2
Discovery & Identification
Enumeration of assets, ports, and services via vulnerability scanning and manual information gathering.
3
Vulnerability Assessment
Analyzing information gathered for all assets and creating an appropriate exploitation plan based on the target network(s).
4
Exploitation
Utilizing the constructed plan to illustrate the true risk that the identified vulnerabilities present to the customer’s network. The exploitation is conducted using both manual attempts and automated tools.
5
Reporting
Provide a report containing high-level takeaways, executive summary, and in-depth details of how each phase proceeded. Review meeting held to go over results with the client.

Vulnerability Scanning
DataSure24’s Security Analysts will conduct internal and external scans to identify, define, and prioritize any security gaps found in a client’s infrastructure. Our vulnerability scanning tools are continuously updated to ensure the newest vulnerabilities can be identified and reported to our client’s technical team.
The frequency of vulnerability scanning is determined by an organization’s size and specific needs. Once scans are completed, Security Analysts analyze and prioritize the scan’s findings and provide clients with a summary report detailing vulnerability and remediation information. A detailed report with all technical information is provided as well.
Assessment Components
1
External Vulnerability Scan
Details security gaps and vulnerabilities posing threats to the organization’s public facing network and external infrastructure.
2
Internal Vulnerability Scan
Details security gaps and vulnerabilities posing threats to internal infrastructure, network and systems.
3
Vulnerability Analysis
An analysis of each vulnerability and identification of recommendations for remediation within the report.
4
POA&M Creation
• Clients are assisted in prioritizing a remediation path.
• Based on the severity of the vulnerabilities, and size of remediation required, Plan of Action and Milestones may be developed, and shared with the client.
5
Reporting
Clients receive a summary and prioritized list of vulnerabilities by risk rating.

Security Awareness Training
People represent the greatest potential security weakness in any organization. With new threats emerging every day, educating employees about cybersecurity risks is an important part of any organization’s strategy to reduce its exposure to potential threats.
Our team will assess your employees’ current cybersecurity awareness and develop a training program that fits your organization and its culture. Training packages are also available based on the specific size and needs of an organization.
Modules may include:
Staff Training Webinar
A member of the DataSure24 team will conduct a live interactive webinar training with your employees.
Virtual Training Session
Interactive virtual trainings cover specific topics, including password best practices, email and browser security, phishing, avoiding malicious downloads, and compliance.
Phishing Campaign
A customized phishing simulation is conducted to determine employees’ likelihood of clicking on malicious emails or links that could threaten the organization.
“Clicker” Training Session
Employees who failed to identify a phishing threat and clicked on bait during a campaign will receive additional training.
Scam of the Week Email
News stories relating to security breaches and threats are sent to employees on a weekly basis to raise awareness.

Professional Services
At a time when cyberattacks are putting businesses of all sizes, from all industries, at risk of a breach, DataSure24’s security analysts provide visibility and vigilance by monitoring an organization’s critical infrastructure and data for malicious and threatening activity 24/7.
This allows organizational leaders to know what’s happening in real time, so they can respond quickly to potential threats. Clients receive protection against potential breaches, including malware, ransomware, and other cyberattacks.
Rapid Response Team
Our 24/7 team is deployed immediately when clients are experiencing a breach. We will provide deployment of our scanning appliance and monitoring equipment to alleviate the security breach rapidly.
Incident Response and Remediation
Rectify any issues at client sites resulting from breaches or vulnerabilities. We will identify a path to remediation for our clients and prioritize recommendations based on risk.
Technical Project Consulting
Any IT security-based project work that organizations do not have the resources to complete, including maintenance of systems.
Policies and Procedures
DataSure24 performs a thorough review of our clients’ policies and procedures surrounding IT and security. From the review, we develop a listed summary of improvements to be made to existing documentation, and identify which documentation is missing and requires creating. DataSure24’s Professional Service team can develop and create these policies and procedures as requested.

24/7 Managed Detection & Response
DataSure24’s Western New York-based Security Analysts monitor an organization’s critical infrastructure and data for malicious and threatening activity 24/7. This allows an organization to know what is happening across its environment in real time, protecting clients against breaches, including ransomware, zero-day exploits (attacks that occur as soon as a software weakness becomes known) and other emerging threats.
The Steller Cyber Open XDR platform that drives the DataSure24 24/7 Managed Detection & Response (MDR) service will tie the other platforms and technologies together to leverage their capabilities and bring information together to provide our clients with an unparalleled level of visibility into the operational effectiveness of its cyber defenses.
24/7 Managed Detection and Response components include:
24/7/365 Security Monitoring
DataSure24’s security analysts provide continuous monitoring of an organization’s environment, including its network, servers, workstations and network devices, and notify clients of potential security notifications and potential security events.
Incident Detection & Response
Risk investigation and mitigation, quickly identifying action to be taken with your team .
Network Intrusion Detection
Network-based monitoring, creating alarms for any malicious activity identified on the network
Host Intrusion Detection
Host-based monitoring of individual machine activity, alerting DataSure24’s security analysts of any malicious activity.
File Integrity Monitoring
Tracks and notifies DataSure24 Security Analysts of any changes to key files and critical data.
Monthly Internal Vulnerability Scanning
Internal infrastructure is scanned on a monthly basis using the Nessus vulnerability scanning tool to identify newly discovered vulnerabilities and security gaps that can be exploited to compromise the organization. DataSure24’s security professionals analyze the scan results and recommend remediation paths as needed.
Log Aggregation & Correlation
Once critical information systems are defined, plug-ins are enabled to comprehend and parse the information. This significantly aids not only the intrusion detection system, but end user capability to correlate multiple events across the defined information systems.

Dark Web Scanning
DataSure24’s Security Analysts provide continuous searching, monitoring, and reporting of our client’s credentials on the part of the web that Google doesn’t see—the Dark Web.
Using the monitoring tool Dark Web ID, our Dark Web Scanning service identifies compromised usernames and passwords. This provides us with critical knowledge used to protect our client’s most valuable digital assets, their credentials, and help reduce the risk of cyberattacks, data breaches and identity theft.
Security Analysts conduct a comprehensive scan of the Dark Web, including:
Proactive Monitoring
Dark Web ID monitors a company’s domain regularly, based on an individual client’s needs.
Similar Passwords
Employees commonly use the same passwords for multiple logins, which puts their company at high risk for further exposure.
Reporting
Clients receive valuable information, sometimes eye-opening, regarding company credentials stolen by hackers.
Recommendations
Depending on the severity of the report’s findings, we may offer additional insight and recommendations related to best practices for password and online behavior. For example, ensuring users’ passwords are unique for each software or platform used, or not using work email for personal use.

Rapid Incident Response
In the event of a breach, it is important to identify critical next steps and minimize the disruption created by the cybersecurity incident. Our Incident Response (IR) team can be deployed in less than 24 hours to coordinate response management, begin containment, assess damage and facilitate the remediation and recovery process.
We will develop a comprehensive plan to contain the incident, eradicate the cause and recover operations. This plan is continuously updated throughout the engagement so that key stakeholders understand what systems were impacted and have insight into availability, estimated recovery time and overall response progress. Our process involves:
- Containment Guidance
- Damage Assessment
- Recovery
- Remediation Eradication
- Post-Incident Activity
What happens if I’m having a security incident?
1
Containment Guidance
Identify hacker activity
Determine an appropriate containment strategy
2
Damage Assessment
Identify and evaluate damaged systems
Investigate what data was accessed and who was responsible
3
Recovery
Restore and return affected systems and devices into your business environment
Test and verify that infected systems are fully restored
4
Remediation Eradication
Systemically remove the issue from your systems
Present a plan of action to remediate and close security gaps identified during the incident response
5
Post Incident Activity
Supply a detailed report reviewing the entire incident response process
A meeting can be conducted to debrief and cover the scope of the incident
