The Standards for Safeguarding Customer Information (Safeguards Rule) requires covered financial companies to develop, implement, and maintain an information security program with administrative, technical, and physical safeguards designed to protect customer information. Additional requirements, related to Section 314.4, are slated to go into effect June 9, 2023.
Not all industries, or even all institutions within individual industries, are subject to regulatory compliance. That doesn’t mean, however, that cybersecurity should not be a business priority. More importantly, business leaders must not confuse regulatory compliance with security. While non-compliance by financial institutions can result in fines, the stakes for a proper security program are much higher. Unprepared organizations will become easy targets for cyberattacks. As mentioned in October’s Brainbytes, earlier this year the debt-collection company Professional Finance Company, Inc. reported a data breach which impacted 657 healthcare providers across the U.S., and 1.9 million patient records. Numerous high-profile data breaches and ransomware attacks have cost millions of dollars to American businesses and affected the data of millions of customers.
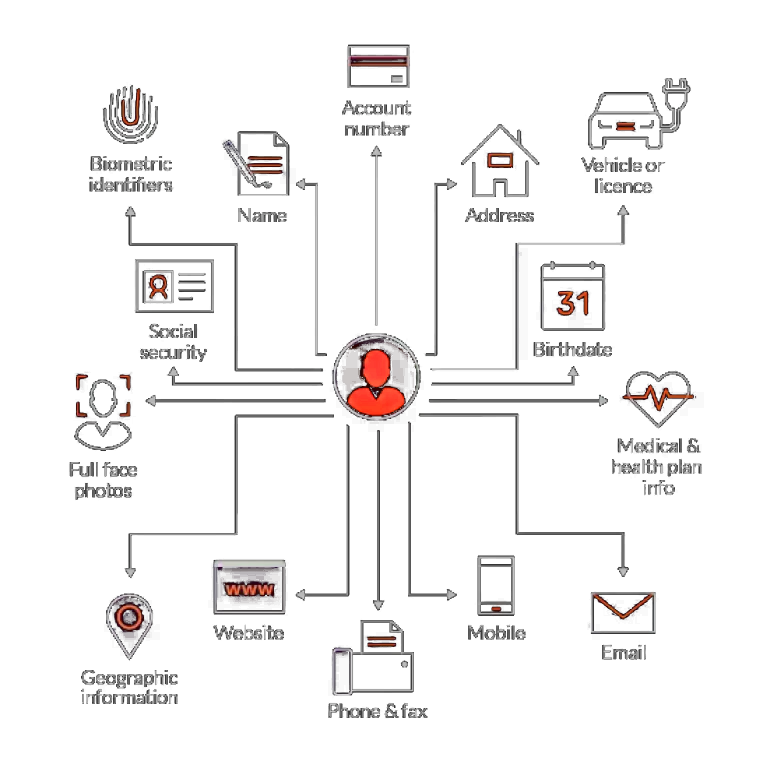
What is PII?
In just the past 20 years, national and international data breaches have affected hundreds of millions of individuals. In fact, according to UpGuard, together, 10 of the most impactful data breaches in the United State’s financial service history compromised Personally Identifiable Information (PII) of more than 485 million people and almost 800,000 businesses. The breached data varied by attack, but together included almost a dozen different types.
Armed with this information, a wide range of cybercrime is possible, including identity theft, ransomware attacks and malware injection.
This makes it crucial to put an appropriate cybersecurity program in place for your business. Again, when developing a program, it’s important to not confuse regulatory compliance with security. In addition to regulatory frameworks, organizations must implement additional cybersecurity systems that specifically address the vulnerabilities facilitating data breaches.
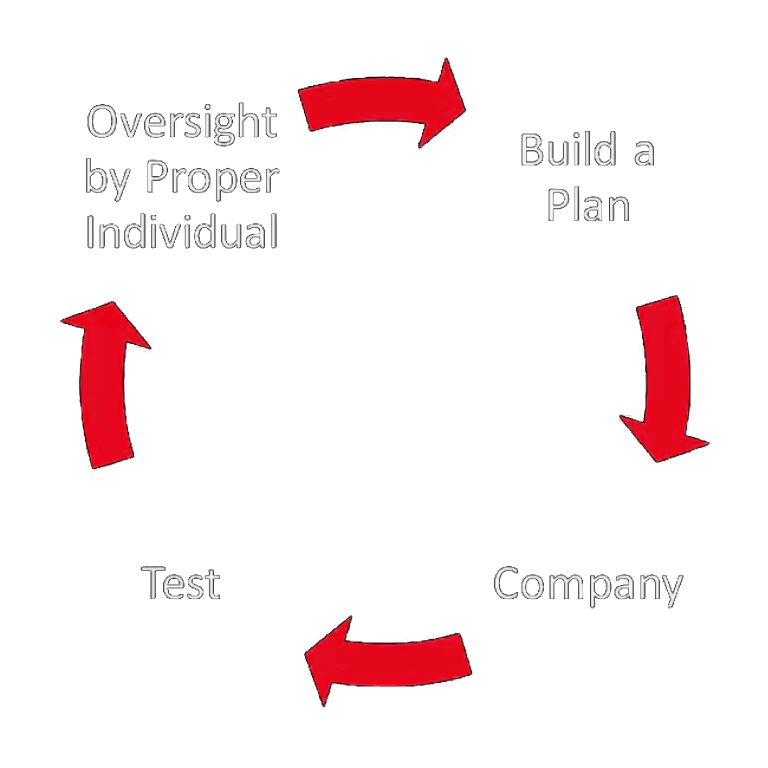
The Proper Way to Build a Cybersecurity Program
Ensure all of these steps are taken. And then checked, and rechecked. Think of this as the rinse and repeat steps in program development and implementation.
The goals of your plan:
- The internal processes your company will activate in response to a security event;
- Clear roles, responsibilities, and levels of decision-making authority;
- Communications and information sharing both inside and outside your company;
- A process to fix any identified weaknesses in your systems and controls;
- Procedures for documenting and reporting security events and your company’s response; and
- A post-mortem of what happened and a revision of your incident response plan and information security program based on what you learned.
Company decision makers, especially those with in-house IT department, will likely look to do this internally. And it’s certainly possible. However, compliance is essential, so companies who don’t have dedicated IT personnel or whose IT department lack the experience, training, or manpower to oversee this program need an alternative solution.
Staff could do vulnerability scans and a qualified individual (I.e. lower tier cybersecurity personnel) could serve as the CISO. Again, it’s difficult for internal security teams to be vigilant for insider threats because they’re already exceeding their bandwidth with risk management tasks. Is it worth the risk for staff to take on program oversight as well?
Learn from the Mistakes of Others
Not sure what to include in your plan? Besides implementing a data protection solution specific to financial services, one of the best methods of mitigating data breaches is learning from the mistakes of others.
In addition to security, software, and hardware updates, other important lessons to note are:
- Ensure thorough internal and external vulnerability scans, and address all, regardless of how simple the vulnerabilities are.
- Regardless of how sophisticated your security program is, basic lapses in system maintenance can lead to data breaches.
- Information not considered highly-sensitive (data commonly exchanged during the normal course of business) was accessed
- Staff are often unaware of cyberthreats, and even less likely to deal with them. Implement cyber threat training in the workplace
- Humans will always be the weakest links in a cybersecurity program. To preserve security control investments, financial services must implement cyber threat awareness training in the workplace.
- Look for signs of employee dissatisfaction; Malicious actions could easily be mistaken for legitimate daily tasks. due to day-to-day tasks,
- It’s also difficult for internal security teams to be vigilant for insider threats because they’re already exceeding their bandwidth with risk management tasks.
- Secure all privileged access
- Streamline Vendor Risk Management –
- Limit login attempts
- Use device cookies
- Don’t reveal correct credentials – Prevent login fields from confirming which specific details are correct.
- Use CAPTCHAS
In general, good practices for better security should always include, but are not limited to, the following:
- Annual penetration tests
- Security audits
- Updated incident response plans
- Cybersecurity training
Does your company have the right cybersecurity plan in place? Contact us for more information on how our customizable services may help protect your business.
Posted by Katie Cassens
